Now that I have captured your attention with this title that could be described as gently sensational, let me explain more concretely the subject of this article.
Context and objectives
In recent weeks, as I delved back into IT governance, I realized it was time to share the reality on the ground regarding B2B SaaS.
Whether you are in the design phase or already in commercialization, you may have noticed: selling to a large company is nothing like B2C. The gap is significant.
If you have ever prospected a mid-sized or large company, you may have experienced the infamous 'IT Director's Veto', sometimes without any explanation, even though the business teams loved your product.

It's frustrating, but logical. The IT Director is not there to block innovation, but to protect their fortress. Constantly solicited, they unfortunately do not have the time to educate every vendor on why their solution does not pass security barriers.
The goal of this article is to provide you with this missing framework (outside of On-Premise). I will list the essential technical prerequisites for your solution to be technically validated.
Meeting these criteria will not guarantee your commercial success. Your product must be good above all. But it will prevent you from being disqualified before you even have a chance to prove yourself.
If this guide allows even one of you to sign your first major account, I will have accomplished my mission.
Who am I?

Nicolas Mulot
CTO as a Service
With 14 years of experience in development, including 8 as a Lead Dev and CTO of solutions SaaS, I have led projects of all sizes for various clients. Familiar with security audits and compliance requirements, I decode for you what IT Directors really expect from software to transform the technical constraints of large companies into business opportunities.
Who is this article for?
This article is for you if you are creating a B2B SaaS software, or if you are already marketing a solution but have faced rejection from IT Directors of SMEs, mid-sized companies, or large enterprises.
Depending on your profile, reading this article will provide you with different insights:
Lead Devs, Lead Techs, and CTOs
To understand the technical requirements of large companies and master the vocabulary that speaks directly to IT Directors. This article will help you build a coherent technical roadmap to make your solution "Enterprise Ready."

PMs, CPOs, CEOs, and Decision Makers
To anticipate the technical steps to take and the resources to engage based on your target market. The topic may seem complex, but hang in there even if you don't master all the jargon: it's the substance that matters. Think of this document as a survival guide for B2B SaaS, which will help you save your resources by aiming accurately and at the right time.

CIOs and IT Directors
To confront your usual reading grid, audit the current state of your application portfolio, or simply review certain market standards.
Introduction
The Cultural Gap between Startup Agility and Large Account Rigor

In today's technology landscape, a fundamental dichotomy persists between the startup ecosystem, characterized by radical agility and rapid iteration, and that of large companies with more than 5,000 employees, governed by stability, systemic risk management, and regulatory compliance.
A Chief Information Officer (CIO) of such an organization does not primarily have the responsibility for adopting technological innovation. What matters most to them is the preservation of the integrity of the company's information assets and ensuring large-scale business continuity.
When a B2B startup presents a promising SaaS (Software as a Service) solution capable of revolutionizing a company's business processes, the initial enthusiasm of business units often clashes with the harsh realities of technical and security considerations during the IT due diligence phase. The CIO will not only look at the features, the user interface, or the promise of immediate added value. They will assess the structural maturity, operational resilience, legal compliance, and the vendor's ability to seamlessly integrate into a complex and interconnected Information System (IS).

The enterprise software market has undergone a profound transformation over the last decade. The era when innovation was done in "pirate mode" (Shadow IT: using IT tools without approval) is over for large accounts concerned about their governance. Today, compliance expectations — such as SOC 2 or ISO 27001 certifications — have become standard prerequisites well before advanced funding rounds, where they once served as late maturity differentiators. For software to be classified as "Enterprise Ready," it must bridge the chasm that separates the minimum viable product (MVP) from the audited critical infrastructure capable of supporting the load and requirements of a multinational organization.
This article aims to detail the technical, security, legal, and operational requirements that a startup CTO (Chief Technical Officer) must integrate into their roadmap to hope to sign a framework contract with a large company. It relies on market benchmarks, the demanding standards of CIGREF (Club Informatique des Grandes Entreprises Françaises), the recommendations of ANSSI (National Agency for the Security of Information Systems), and the best practices observed in the industry. This document is designed as a management tool to align your technological trajectory with the sovereignty and security imperatives of large companies.
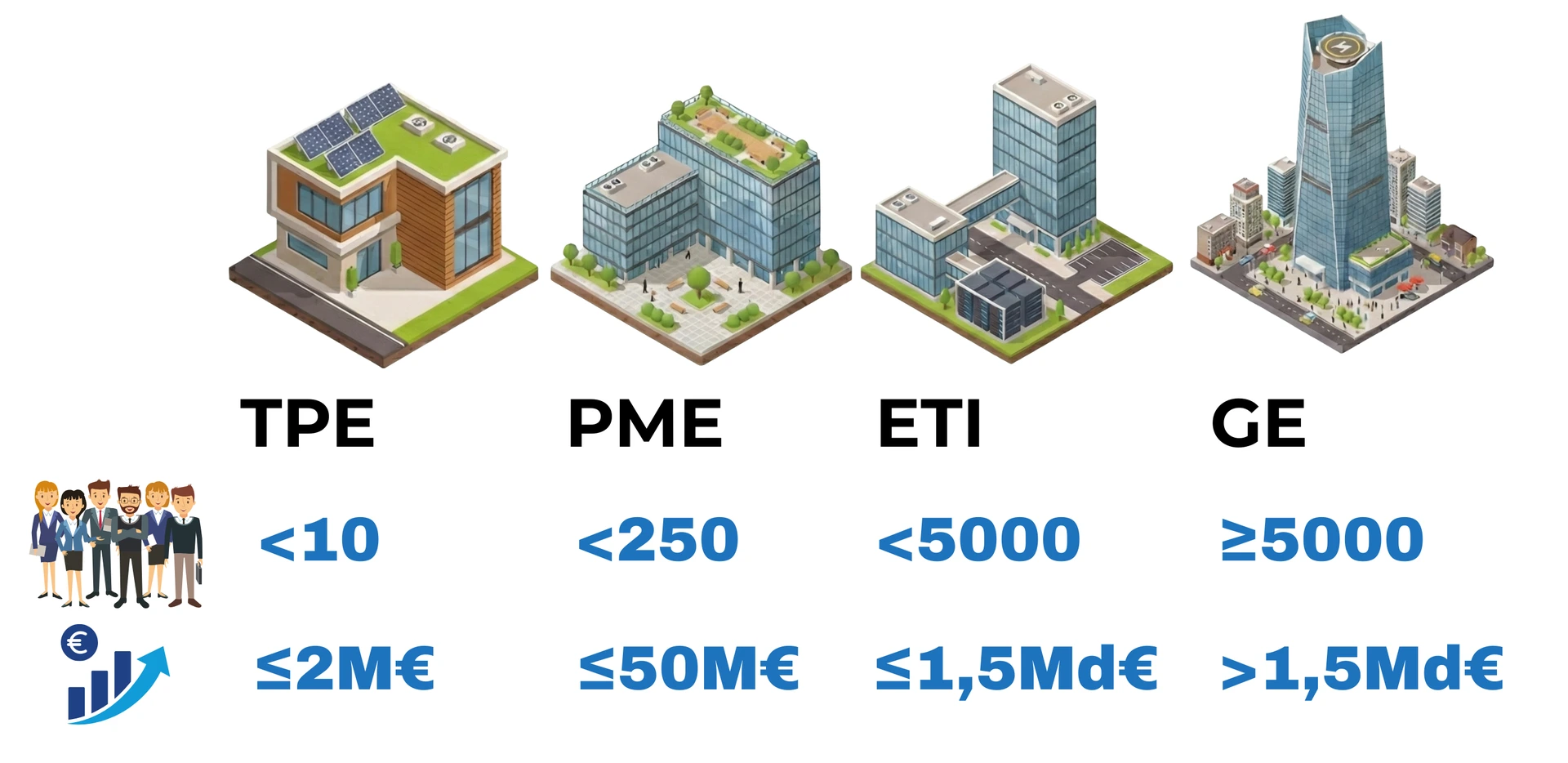
In marketing, defining your 'Persona' is essential. Technically, the logic is the same: you need to identify the target company size to allocate your technical resources in the right place, without waste.
To help you visualize the climb ahead, I will detail the specific requirements for each segment (micro-enterprises, small and medium-sized enterprises, intermediate-sized enterprises, and large enterprises) at the end of this page. The goal of this article is to get you into the mind of an IT Director: understanding their blockages is the best way to turn your security audit into a mere formality.
1. Governance, Compliance, and the "Trusted Cloud"

For a large European company operating in a strict regulatory environment, data sovereignty and compliance are not just boxes to check, but existential pillars. Even before examining the technical architecture or the quality of the code, IT Directors will audit the governance of data and the trust structure proposed by the vendor.
1.1. Compliance

If security reassures the CIO, compliance reassures the DPO (Data Protection Officer) and the Legal Director. Without these validations, no contract will be signed, even if your technology is revolutionary.
Here are the 4 acronyms that govern the B2B market today:
GDPR (The Common Framework)
This is the minimum requirement forany companyoperating in Europe or processing data of European citizens.
For whom?
Everyone (micro-enterprises, SMEs, mid-sized companies, large enterprises).
The impact for you:
DPA (Data Processing Agreement):
You must provide a contractual annex on data processing.
Right to be forgotten:
Your architecture must allow for the complete deletion of a user's data upon simple request.
NIS2 (Cybersecurity for critical sectors)
Recently enacted, this European directive aims to secure critical entities (Energy, Transport, Banking, Health, Water, Digital Infrastructure, B2B ICT service management, etc.) with more than 50 employees or more than 10 million in revenue. I have simplified the conditions a bit to take the minimum thresholds, but you can find the exact conditions here.
For whom?
If you sell to "Essential" or "Important" Entities. As a SaaS provider, you are part of the "Supply Chain" of these large groups. They now have a legal obligation to audit the security of their suppliers.
The impact for you:
You will be required to have rigorous incident management (notification within 24h/72h) and proven security measures (often aligned with ISO 27001).
DORA (The Resilience for Finance)
TheDigital Operational Resilience Actis specific to the financial sector (Banks, Insurance, FinTech).
For whom?
If you sell to financial institutions.
The DSI requirement:
DORA not only requires security but alsoResilience..
How does your service restart after a disaster?
Do you have an exit plan (Exit Strategy)? If your startup goes bankrupt tomorrow, how does the bank recover its data to migrate it elsewhere (Reversibility)?
HDS (Health Data Hosting)
This is a specific French certification for health data.
For whom?
If your SaaS solution deals, directly or indirectly (processing or backup), with personal health data (HR context, occupational medicine, insurance, employee well-being), the "Health Data Host" (HDS) certification is a strict legal obligation in France (Public Health Code), and not just a "best practice."
The impact for you:
The HDS certification is based on the ISO 27001 framework and adds specific requirements regarding sovereignty, patient rights, and enhanced protection. It is divided intotwo areas that the CTO must master. :
Physical infrastructure host:
Concerns data centers (e.g., AWS, OVHcloud are certified).
Managed hosting provider:
Concerns the SaaS publisher that administers the platform and manages backups.
A SaaS startup operating on AWS (certified HDS infra) must still obtain its own HDS certification (managed provider) to be compliant. Ignoring this legal nuance exposes both the client and the provider to severe criminal penalties.
1.2. The Certification Standard: ISO 27001 and SOC 2

It is imperative for any CTO to understand that certification is no longer an option reserved for established players. Market data indicates a massive acceleration in compliance: 72% of funded SaaS startups now secure SOC 2 compliance even before their Series A fundraising, compared to only 31% in 2020 (according to Bigmoves Marketing). This significant trend reflects the growing demand from major clients who refuse to integrate weak links into their digital value chain.
ISO/IEC 27001: The Foundation of Security Management
ISO 27001 remains the international standard of reference for large European organizations. It not only certifies technical security at a given point in time, but also validates the existence and effectiveness of a living and dynamic Information Security Management System (ISMS).
Expectation:Enterprise CIOs may require not only to see the valid certificate but also the Statement of Applicability (SoA). This document is crucial as it lists the security measures you have chosen to implement or exclude. An unjustified exclusion of a critical control (such as cryptographic key management) will be immediately flagged as a major risk.
Proof of maturity:The certification demonstrates that security is driven at the management level, that there is a formalized risk management process, and that continuous improvement is integrated into the company's processes.
SOC 2 Type II: The Proof by Experience
Although of North American origin (AICPA), the SOC 2 (Service Organization Control) report has become essential, often preferred over ISO 27001 for its technical granularity on Cloud services.
Type I vs Type II:A SOC 2 Type I report only certifies that your controls are well designed at a specific point in time. For a large account, this is insufficient. They will certainly require a SOC 2 Type II report, which audits the operational effectiveness of these controls over an observation period (usually 6 to 12 months). This proves that you are not just writing procedures, but that you are applying them daily (for example, that access reviews have indeed taken place every quarter without exception).
Trust Service Criteria:Beyond Security (mandatory common criterion), CIOs of large companies are particularly attentive to the criteria of Availability (for critical applications) and Confidentiality.
1.3. Digital Sovereignty and Trusted Cloud (CIGREF Reference)

The geopolitical (U.S. Cloud Act, Chinese intelligence laws) and regulatory context has pushed large French companies, through CIGREF, to define strict criteria for the "Trusted Cloud." The goal is to protect against the extraterritoriality of foreign law that could allow a foreign power to access your clients' sensitive industrial data.
The standard tender from CIGREF now includes a specifications document with over 250 technical and legal criteria to assess this level of trust. As a SaaS provider, you must clearly position yourself on this chessboard:
Legal Immunity:
Are your data (and those of your subcontractors) subject to the Cloud Act? If you host data on an American hyperscaler (AWS, Azure, GCP), even in data centers located in Paris or Frankfurt, they remain potentially accessible to U.S. authorities through the parent company.
Compensatory Measures:
If you use these platforms (which is the case for most startups), large companies will require strong technical measures to ensure their sovereignty, particularly encryption for which they will hold the keys.
BYOK (Bring Your Own Key):For the most sensitive data and to ensure immunity against the Cloud Act, the ability to manage their own encryption keys (via dedicated AWS KMS or Azure Key Vault) is a major differentiator. This technically ensures that in the event of a judicial requisition or intrusion at your premises, the data remains unreadable without their key, which they can revoke at any time. This is often the ultimate argument to convince a reluctant CISO.
Transparency of the Value Chain:
You must map the entirety of your subcontracting chain. If your service goes through an API hosted in the United States or if your technical support is operated from a country that does not comply with GDPR, this must be disclosed. Opacity on this point is an immediate disqualification reason.
💡 Tip!
If you're aiming for NIS2, DORA, or HDS regulations, don't reinvent the wheel; take the opportunity to also pursue ISO 27001 certification. It's an international standard that covers a large portion of the requirements of these regulations. Simply stating "We are ISO 27001 certified" will help expedite compliance discussions.
2. The Security Assurance Plan (SAP) and the Defense Architecture
The Security Assurance Plan (PAS) is the centerpiece of the technical relationship between a startup and a large account during the contractual and operational phase. Unlike a commercial brochure "Security Whitepaper", the PAS is a living, enforceable contractual document that describes how you specifically secure the client's perimeter and data.
2.1. Structure and Detailed Requirements of the PAS

According to the guidelines of ANSSI and the practices of large industrial groups (such as TotalEnergies or banking sectors), the PAS must comprehensively cover the following areas, and the CTO must be prepared to defend each point before the client's cybersecurity experts.
Critical Components of the Security Assurance Plan (PAS):
Scope of the PAS | Technical and Organizational Requirements for the Startup | Expected Evidence |
|---|---|---|
Cybersecurity Governance | Identification of the CISO (or security officer) at the startup. Data classification policy. | Cybersecurity organizational chart, IS security policy (PSSI). |
Isolation (Tenant Isolation) | Technical description of client data isolation. How do you ensure that a breach on Client A does not allow access to Client B's data? (Logical isolation via tenant_id in all SQL queries, encryption with a unique key per tenant). | Detailed architecture diagrams, code review of isolation mechanisms. |
Vulnerability Management | Monitoring Process (CERT, CVE, NVD). SLA (Service Level Agreement: service level agreement) for vulnerability remediation (e.g., Critical < 48h, High < 7d). Patch management policy for OS and third-party libraries. | Automated scan reports, examples of remediation tickets. |
Development Security | Integration of security into the Software Development Lifecycle (SDLC). Use of SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) in CI/CD. Training of developers in Secure Coding (OWASP). | Screenshots of CI/CD pipelines showing blocking security steps. |
Cryptography | Standards used (AES-256 for storage, TLS 1.2 or 1.3 for transit). Key lifecycle management (rotation, revocation). Use of HSMs (Hardware Security Modules) or cloud KMS (Key Management Service). | Encryption policy, matrix of encrypted flows. |
Sécurité et Accès | Who has access to production? Background checks for teams. JML (Joiner/Mover/Leaver) process. Principle of least privilege. | Access management policy, anonymized list of administrator profiles. |
Incident Management | Detection, qualification, and notification procedure. Data breach notification commitment (< 24h or 48h according to GDPR). | Crisis management flowchart, crisis communication templates. |
2.2. Audits, Pentests, and Continuous Transparency

Trust does not exclude control. Companies no longer accept to "take on faith" or settle for a two-year-old report.
Recurring Penetration Tests (Pentests):You must conduct comprehensive penetration tests (Grey Box) on your application and APIs at least once a year, and after each major update. These tests must be conducted by qualified third-party auditors (the PASSI qualification in France is a quality assurance recognized by ANSSI). Companies require access to the executive summary and the letter of confirmation for the remediation of critical vulnerabilities.
Audit Right (Audit Clause):Certain contracts with large companies will include a clause allowing them to audit (themselves or through a third party) your compliance. Although rarely activated for small startups if the SOC 2 reports are clean, refusing this clause is a major red flag regarding the opacity of your operations.
Code and Dependency Scanning (SCA):With the rise of attacks on the software supply chain (such as Log4j), companies expect you to monitor your open-source dependencies. The integration of SCA (Software Composition Analysis) tools like Snyk or Dependabot is monitored to ensure they do not inherit known vulnerabilities through your libraries.
2.3. Application Security, API Protection, and WAF

Your infrastructure must be robust against external threats. For a large company, downtime caused by a DDoS attack on your service has immediate financial repercussions.
Web Application Firewall (WAF), DDoS protection, and CDN
Using a WAF combined with a DDoS protection solution and a CDN (Cloudflare, AWS WAF, AWS Shield, Google Cloud Armor, Akamai, etc.) is necessary. Your WAF must be configured to automatically filter common attacks from theOWASP Top 10. This is an essential checkbox in the security questionnaires of major accounts.
Rate Limiting
You need to implement intelligent rate limiting at multiple levels (IP, User ID, Token). In a multi-tenant architecture, this is the only protection against the "Noisy Neighbor" problem, where a legitimate but dysfunctional client saturates your resources to the detriment of others. Limiting strategies should be granular (by endpoint, by HTTP method) so as not to impact the legitimate user experience.
Clearly document your API call limits (quotas, burst). In a corporate context, they must be assured that their batch processing at night will not be randomly blocked by opaque limits.
API Security
Your APIs, often the heart of Enterprise integration, must be protected against credential stuffing and scraping. Strong authentication (OAuth2, mTLS for B2B) is non-negotiable.
3. Identity and Access Management (IAM): The Single Sign-On
For a large enterprise, manual management of user accounts (creation via email, shared password, manual deletion) is an operational heresy and a critical security flaw. Integration with their information system must necessarily go through a robust identity federation.
3.1. Single Sign-On (SSO): The Absolute Requirement

SSO is not a premium "Enterprise" feature that can be sold as an expensive optional add-on ("SSO Tax") without friction; it is a basic hygiene prerequisite for any large deployment.
Standard Protocols:The company must be able to connect your application to their enterprise IdP (Identity Provider), which is usually Microsoft Azure AD (Entra ID), Okta, or PingIdentity. You must natively support SAML 2.0 or OIDC (OpenID Connect). Proprietary solutions or homegrown hacks are prohibited for maintainability and security reasons.
User Experience and Security:SSO eliminates password fatigue for employees and allows them to enforce their own complexity and rotation policies. More importantly, it centralizes the control point: if they detect a compromise, they block the account on their IdP and access to your SaaS is cut off instantly.
Multi-Factor Authentication (MFA):If, for technical reasons (off-domain admin access, technical accounts), SSO cannot be enabled for certain users, your application must offer and enforce MFA (TOTP, WebAuthn/FIDO2). The absence of MFA is a "No-Go" for any application hosting sensitive data.
3.2. Automated Provisioning and Lifecycle (SCIM)

This is often the precise point where startups technically fail to meet the requirements of large accounts. SSO manages authentication (the entry), but who manages the account lifecycle (onboarding, role changes, departures)?
The Risk of "Ghost Accounts":When an employee leaves a company, their access must be revoked everywhere. If your application only supports JIT (Just-in-Time) SSO that creates the account on the fly, it will never know that the employee has left. The account remains active in your database, potentially accessible through backup methods or persistent API tokens. This is an unacceptable data leak risk (Zombie Accounts).
The SCIM 2.0 Standard (System for Cross-domain Identity Management):You must support the SCIM protocol to allow enterprise directories to drive ("Push") the creation, updating of attributes (name change, service change), and especially the deactivation of accounts in your SaaS. Automating offboarding is a key validation criterion for operational security teams.
3.3. Role Model (RBAC) and Segregation of Duties
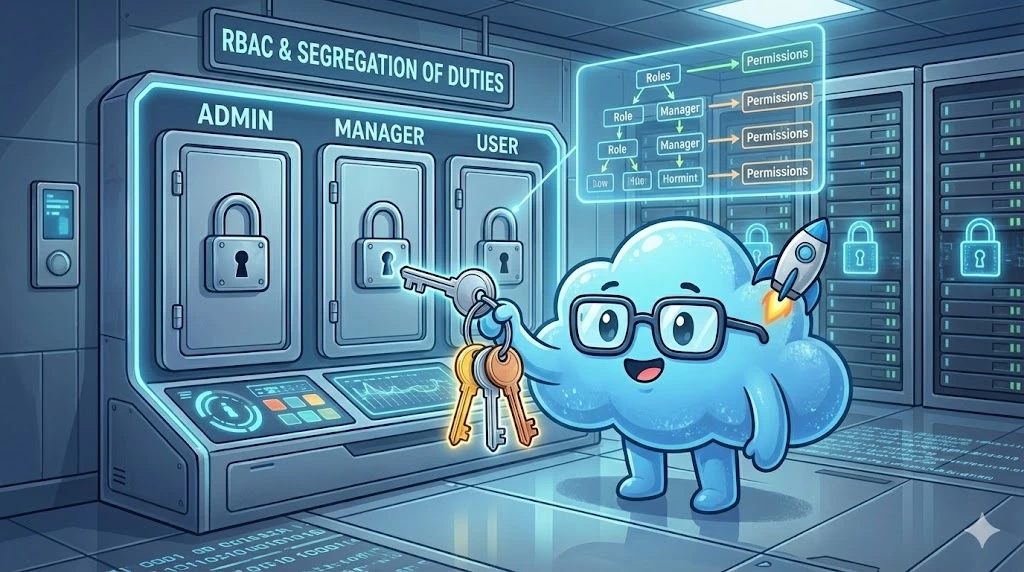
The structure of a large company is inherently hierarchical and segmented. The binary model "Admin" vs "User" is insufficient.
Granular RBAC (Role-Based Access Control): Companies need rich predefined roles (e.g., Read-Only, Editor, Technical Admin, Billing Admin, Auditor) and ideally the ability to define custom roles based on atomic permissions.
Segregation of Duties (SoD):For critical applications (Finance, ERP, HR), ensure that the same user cannot accumulate conflicting rights (e.g., initiate a payment and approve it).
Access visibility:They need tools to audit "who has access to what" in your tool. An exportable report of user rights is necessary for their periodic access reviews.
Management of privilege escalations:All critical privilege escalations (e.g., moving from Reader to Technical Admin) must directly trigger an alert to the RSI, the DSI, or the competent persons. This allows them to quickly detect an unwanted privilege escalation and be proactive.
4. Data: Reversibility, Logging, and Auditability
The data belongs to the client. This principle must be technically translated into a total capacity for recovery and traceability. The "Vendor Lock-in" of the data is a major concern for IT managers.
4.1. The Reversibility Clause and Data Export
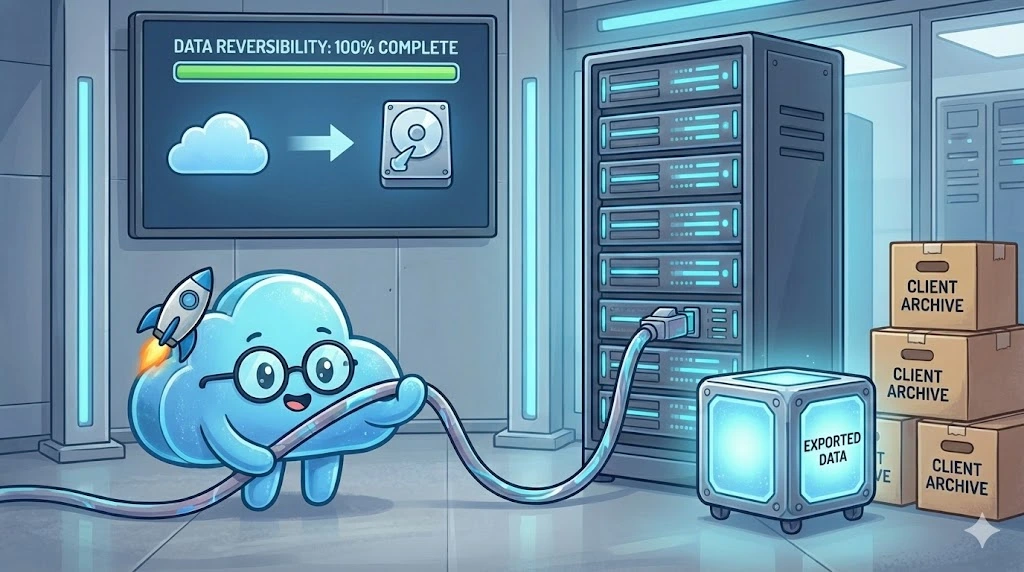
Reversibility is the technical and contractual ability to recover all of the company's data at the end of the contract to migrate it to another system or internalize it. This is a critical point monitored by CIGREF and legal experts.
Standard and Documented Formats:The export must not be an unusable raw SQL "dump" or an obscure proprietary format. An open standard file format will be required: JSON, CSV, XML for structured data, and native formats for files (PDF, DOCX). The data schema must be documented to allow for re-ingestion.
Completeness of the Scope:The export must include entered data, data generated by the system (calculations, workflows), metadata (who created what, when), attached files, and audit logs. Everything that constitutes their activity history must be retrievable.
Autonomy (Self-Service):Ideally, the global export function should be accessible in self-service via the API or the admin console for administrators, without requiring the opening of a support ticket that would take weeks. This reassures about your transparency.
4.2.Secure Data Destruction
 Be careful not to confuse the "Right to be Forgotten" (GDPR) which concerns an individual user, with the End of Contract Destruction which concerns the entire client company.
Be careful not to confuse the "Right to be Forgotten" (GDPR) which concerns an individual user, with the End of Contract Destruction which concerns the entire client company.
When the contract ends, the CIO demands absolute assurance that no confidential data (strategy, finances, trade secrets) persists in your infrastructure. The technical challenge? Your backups. It is difficult to delete the data of a specific client in a backup stored on magnetic tape or AWS Glacier without corrupting everything.
The expected solution: The Crypto-Shredding to completely reassure a large account, the ideal is to have an architecture where each client (Tenant) has its own encryption key.
At the time of departure:You do not attempt to overwrite the disks (impossible in the Cloud). You simply destroy the encryption key of the client.
The result:All data, including that present in your historical backups, becomes instantly and mathematically indecipherable.
The proof:You provide a "Certificate of Key Destruction," which legally constitutes data destruction.
4.3. Logging and SIEM Integration (Security Information and Event Management)
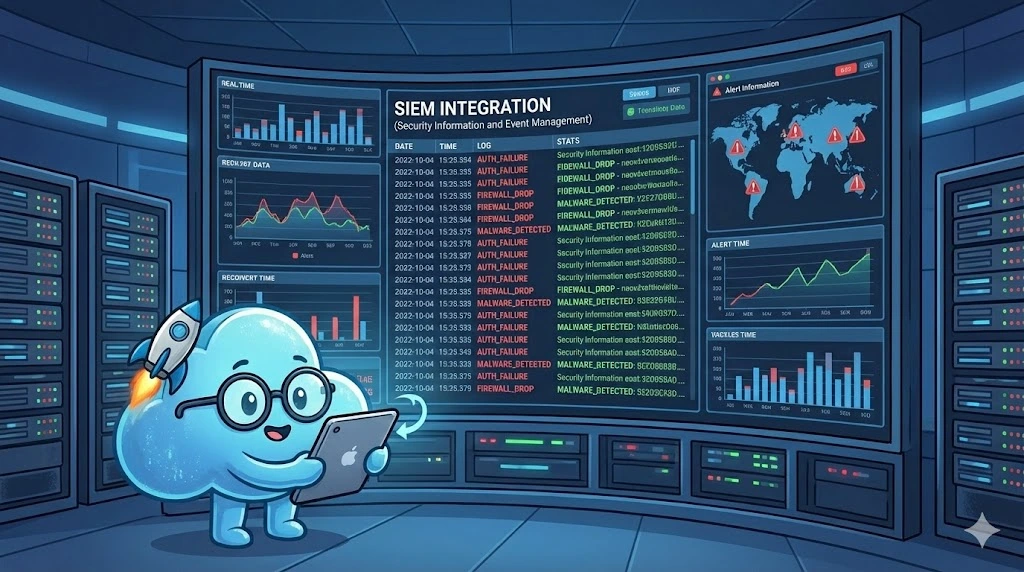
In the event of a security incident or internal investigation (fraud), companies need to know "who did what, when, and from where."
Immutable Audit Logs:Every significant action (login, accessing sensitive data, configuration changes, bulk export, permission changes) must generate a logging event.
Standardized Log Content:Each log must contain at a minimum: precise timestamp (NTP synchronized), unique user identifier (not just a name), source IP address, type of action, targeted resource, and result of the action (Success/Failure/Denied).
SIEM Export Capability:Large companies do not want to connect to your proprietary dashboard to view logs one by one. You must allow automated export of logs to their SIEM (Splunk, QRadar, Azure Sentinel). Standard methods are the REST API for logs (pull) or automatic deposit of flat log files in a secure S3 bucket they control (push). This is a vital requirement for their SOC (Security Operations Center) which must correlate your events with the rest of their SI.
4.4. Encryption at Rest and in Transit
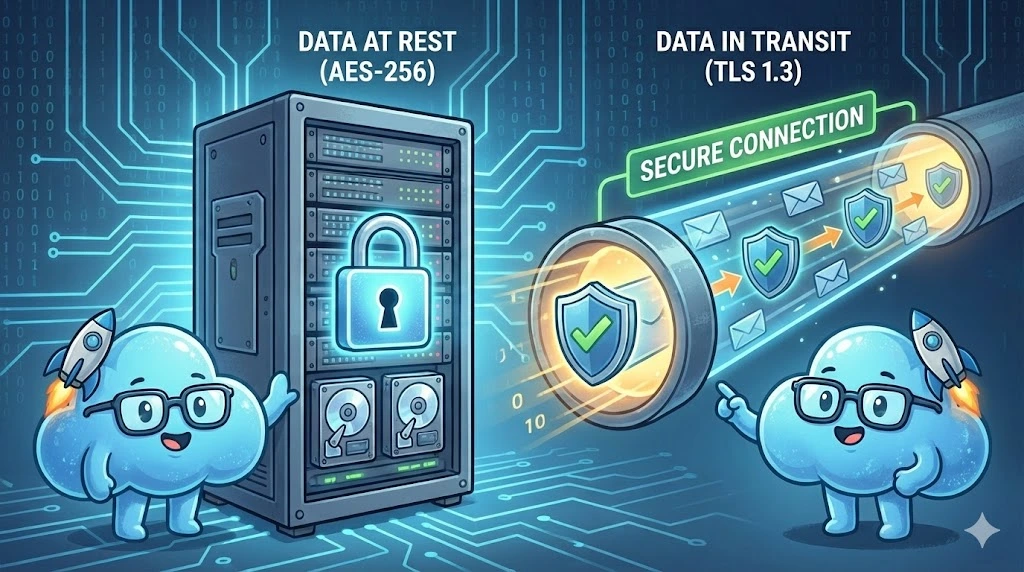
The minimum standard is TLS 1.2 or 1.3 for all network flows (transit) and AES-256 for the storage (at rest) of databases and files.
5. Operational Excellence: SLA, Support, and Continuity
A large company cannot rely on software that "does its best." They purchase a service guarantee and continuity assurance. Downtime has a direct cost on their productivity.
5.1. SLA (Service Level Agreement) and Penalty Mechanisms

An SLA without financial penalties is just a marketing promise without contractual value.
Guaranteed Availability:They generally expect a monthly availability commitment of 99.9% (approximately 43 minutes of maximum downtime per month) for standard tools, and 99.99% for critical tools.
Calculation of Service Credits:The contract must stipulate automatic service credits (credits on the next invoice) in case of non-compliance.
Typical example:10% penalty if availability < 99.9%, 25% if < 99.0%, 50% if < 98.0%.
Clear Exclusions:Scheduled maintenance windows (announced in advance and performed outside of business hours) are generally excluded from the calculation, but they must be reasonable.
Transparency (Status Page):A public or private status page, updated in real-time and historically archived, is mandatory. It must detail the status of various components (API, Front, Workers, Database).
Here are some examples:
5.2. Resilience: RTO, RPO, and Business Continuity Plan (BCP)

In the event of a major disaster (such as a data center fire like OVH Strasbourg, or a massive ransomware cyberattack on your premises), how quickly and in what state will they be able to resume work?
RTO (Recovery Time Objective):Maximum allowable downtime before returning to normal.
SaaS Standard:< 4 hours for critical applications, < 24 hours for non-critical.
RPO (Recovery Point Objective):Maximum acceptable data loss (age of the last restored backup).
SaaS Standard:Tolerance is rarely more than 1 to 4 hours of data loss for transactional systems. For highly critical systems, aim for an RPO close to zero (synchronous replication).
DR Tests:Having a plan on paper is not enough. You must prove that your DR plan is technically tested at least once a year (actual failover or table-top simulation) and provide a brief report of the results.
5.3. Technical Support and Service Levels

A large company is potentially spread across multiple time zones, and it cannot rely solely on email or asynchronous chat support based on a single time zone (e.g., Pacific Time or Indian/Reunion).
Response Times (RTO/RPO)
RPO:Response Time Guarantee
The CIO of a large company does not want just an automatic message but a real human response that shows the request has been properly acknowledged.
RTO:Recovery Time Objective
This is the maximum time before returning to normal. This time is calculated from the reporting.
Types of Maintenance
In order to correctly specify your RTO and RPO, it is important to clearly distinguish between the types of maintenance in your contracts to avoid it costing you dearly contractually.
Corrective Maintenance (The "Priorities" from P1 to P4)
This is everything that falls under "It is not working as expected."
- The situation:The software is broken, there is an error, abnormal slowness, or a typo.
- The obligation:You have a result obligation (to fix) with penalties if you exceed the deadlines (SLA).
Evolutionary Maintenance (The "Feature Requests")
This is everything that falls under "I would like it to do this in addition."
- The situation:The client "Would like a button here", "Would like the export to be in PDF instead of CSV", "Would like to change the header color."
- The obligation:You have no contractual deadline obligation (unless there is a payment and a contract for specific development). It is subject to your product roadmap.
Prioritization of Corrective Maintenance
Enterprise IT departments distinguish blocking incidents (P1 - Production stopped, everyone is blocked) from minor requests.
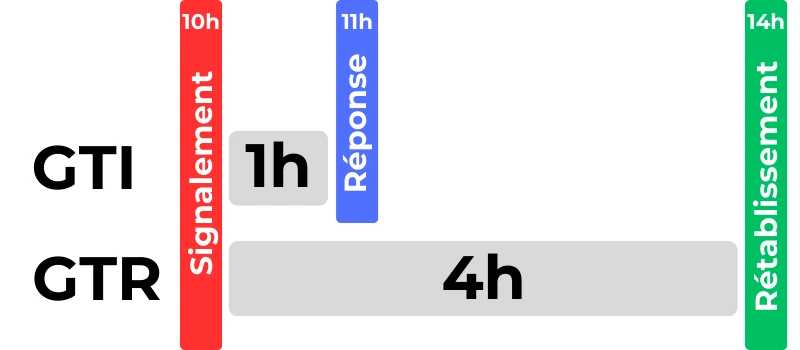
P1: Critical Priority (Absolute urgency)
The situation:"Everything is broken." The application is completely inaccessible (Down), or a vital feature (like payment or login) is no longer working for all users. There is a risk of data loss or a direct and immediate financial impact.
Expectation from IT:All hands on deck. It is expected that your technical teams are on call 24/7/365 until resolution.
Typical SLA:
GTI:Response guaranteed in less than 1 hour.
GTR:Resolution in less than 4 hours.
P2: High Priority (Major but not completely blocking)
The situation:The service is severely degraded (very slow), or an important feature is broken, but there is a painful workaround, or it only affects a portion of users. The business continues, but "it's really creaking."
Expectation from the IT Director:A quick and prioritized response compared to product development.
Typical SLA:
GTI:Response guaranteed in less than 2 hours.
GTR:Resolution in less than 24 hours (1 business day).
P3: Medium Priority (Standard bug)
The situation:A functional bug that hinders use but does not prevent work. Example: an export function that sometimes fails, or a poorly placed button.
Expectation from the IT Director:That it be planned in the next sprint or corrective patch.
Typical SLA:
GTI:Response guaranteed in less than 24 hours (1 business day).
GTR:Resolution in less than 30 business days.
P4: Low Priority (Cosmetic)
The situation:Anything related to finishing touches (Spelling mistakes, visual alignment issues, etc.)
Expectation from the IT Director:That it be taken into account.
Attention:If a P4 ticket is opened and 6 months later it is still not fixed, the message sent is: "We are neglecting the details." If you neglect visible details, they will start to fear that you are neglecting security or code quality. A quickly resolved P4 demonstrates your team's excellence.
Typical SLA:
GTI:Guaranteed response in less than 2 business days.
GTR:No firm commitment, but do not neglect these requests that prove your seriousness.
Language and Localization
For a French company, the ability to provide support in French (or at least impeccable technical English) during European business hours is a considerable asset. Outsourcing to specialized BPO providers can help achieve this level of service 24/7 without exploding your costs.
6. Integration, API, and Technical Ecosystem
Your software will not exist in a vacuum. It must fit into a heterogeneous Information System, composed of modern components and "Legacy" systems (ERP, Mainframe). Integrability is a decisive selection criterion.
6.1. "API First" Strategy and Documentation

Integration should not require months of custom development or costly "Professional Services."
API Coverage:Aim for 100% API coverage. Everything that can be done via the user interface (creating an object, launching a process, extracting a report) should be possible via REST or GraphQL API. This allows companies to automate their processes through their orchestration tools (RPA, iPaaS).
Developer Documentation:A static API documentation (PDF) is insufficient. They expect up-to-date standard interactive documentation (Swagger/OpenAPI) with clear code examples.
Webhooks and Event-Driven:For automation, they prefer event-driven architectures. Your system must be able to send Webhooks during business events (e.g., "Contract signed", "User created") to trigger their internal workflows, thus avoiding constant polling of your APIs that overloads both parties.
The API and its documentation should not be an afterthought: they are foundations to be laid from day one ("API First"). To ensure the sustainability of a SaaS, one must anticipatescalingand scalability.
In practical terms, this requires a decoupled architecture (type3-tier): your Backend exposes data via a documented API, which is consumed by your Frontend. This initial rigor will not only allow you to maintain a high-performing web application but also to deploy a mobile application or open your services to partners without having to recode everything.
6.2. Management of Environments and Deployments
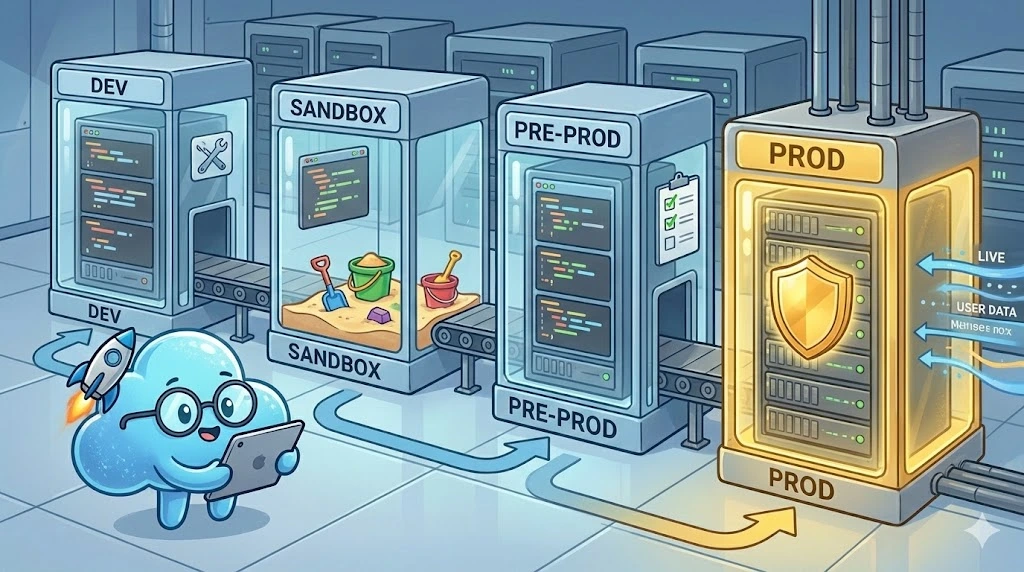
You must structure your architecture with distinct environments that meet specific objectives. The absolute nightmare of an enterprise CIO is to see you perform tests in production. This reflects a dangerously low level of maturity (the infamous"Testing in Prod").
Here is an example of an accepted structure that you can describe in your contracts (SLA) :
The Production Environment (PROD)
It is the "Holy of Holies". It is the real, stable, high-performance, and secure environment where critical business data flows.
Key feature:It must be inviolable by developers (no direct access to the database). This is the environment where your SLA guarantees apply and where daily backups are performed.
Usage: Real and daily use by end customers.
The Staging or Pre-Production Environment (PRE-PROD)
It is the mirror of production. It is used to validate a release candidate (Release Candidate) before it is pushed to production.
Key feature:
It must be "Iso-Prod" (Iso-functional and Iso-architecture). This means it has the same server configuration, the same software versions, and a similar data volume to production.
Usage:
This is where the final non-regression tests and UAT (User Acceptance Tests) are performed before the final deployment.
⚠️ Beware of the GDPR trap!
If you want to have a realistic data volume on your PRE-PROD, never copy the Production database as is. A vigilant IT manager will systematically check if you practice data anonymization. (Data Masking). If it detects the presence of real names, emails, or salaries of its employees in your pre-production environment (which is often less secure or accessible to more developers), it is a major non-compliance that can terminate the contract.
The Development Environment (DEV)
This is the internal environment dedicated to your technical teams. It allows for rapid deployments to test code on a server infrastructure, without impacting stable environments.
Key feature:
It is very volatile. You can break features, restart services at will, and deploy unstable code without any risk and without waiting for it to be tested in PRE-PROD.
Usage:
Allows your developers to technically validate a feature before merging it into the main branch. This saves time for your technical teams' testing, which provides a quality gain for your product.
The Sandbox Environment (SAND BOX)
This is the environment dedicated to your clients. It allows them to test your solution before signing, or to validate technical integrations without polluting their production data. This is often the environment forgotten by startups, yet essential for integration.
Key feature:
It is disconnected from reality. You can create fake data, generate false traffic, and make mistakes without consequences.
Usage:
Allows teams to test the functionality of your application, and their developers to test your API safely.
💡 Important Note
Ideally, your architecture should allow for a secure Sandbox to be instantiated per client. Client A should not see Client B's test data, even if it is just "fake" data.
Zero Downtime Deployment
The phrase"We will shut down the service for 2 hours tonight for the update"has become unacceptable today for a quality SaaS. Clients expect Zero Downtime Deployment (ZDD). Updates to your SaaS should not interrupt service. Modern deployment techniques (such as Blue/Green) are expected to ensure that maintenance is transparent to your users.
7. The Technical Maturity Roadmap
Faced with the exhaustive list of requirements we just reviewed, the temptation is great to want to implement everything immediately. This is a classic mistake that can suffocate your product roadmap.
In an ideal world, all these boxes would indeed be checked from day one. But the reality of a startup is made up of ongoing trade-offs between speed and compliance.
The goal of the matrix below is to help you prioritize. It highlights what is strictly necessary to unlock a signature based on your interlocutor (from small businesses to large accounts), but also on your current resources. It also allows you to assess your technical maturity in relation to what you can expect for each type of fundraising (from Seed to Series B+).
Keep in mind that this table is a compass: while it covers the reality of a large part B2B SaaS publishers, it will need to be adjusted according to your specific context (especially if you are targeting ultra-regulated niches). The idea is not to be perfect everywhere, but to be "sufficiently robust" where your client expects it.
Legend
❗ Mandatory (Regulatory) Legal imperative or strict constraint. It is impossible to deviate from this rule under penalty of sanctions or immediate illegality.
✅ Necessary (Market Standard) Strongly expected to convert this type of client. If this box is not checked, the risk of refusal (No-Go) is very high and your chances of signing decrease drastically.
🚀 Asset (Nice to have) A valued "plus" that reassures the client and can accelerate the sale. However, the absence of this criterion is generally not a blocker for signing.
⬜ Not Relevant Criterion rarely sought or evaluated by this type of client.
Conclusion: Don't try to catch a whale with a fishing rod
If you have made it to the end of this article, you are probably feeling dizzy in front of the mountain of technical prerequisites. This is normal. The gap between a B2C SaaS and a solution suited for Large Enterprises is immense. It is important to keep your feet on the ground.

Now that you have a better understanding of the topic, here are 5 essential points I want to highlight:
1. No-Code has its limits (the glass ceiling)
No-Code tools are great for iterating quickly and validating an MVP. But let's be clear: they will be difficult to deploy in a mid-sized company or a large account. The constraints of auditability, fine security, and data sovereignty imposed by these large players are often incompatible with the closed architectures of these platforms.
2. The entry ticket is expensive
Selling to large companies requires a colossal investment. The technical upgrade represents a significant development cost. This is an entry barrier that should not be underestimated. But investing early in these "invisible" foundations will benefit you in the long run.
3. Make your Tech team a business ally
To sell to large accounts, relational skills are no longer enough: you need to convince demanding technical experts. This is where your CTO and Lead Techs become major assets to support your sales team. Do not confine them to coding: involve them in the final sales phases. They are the ones who will know how to find the words to reassure a CIO and validate the feasibility of contractual promises. A strong synergy between your Sales and Tech teams is often the key factor in unlocking these complex signatures.
4. The AI trap: Lever or Replacement?
As AI floods the market, many founders think they can reduce their technical team to save costs. This is a major strategic mistake. As you have seen in this article, the requirements (Compliance, Security, Ops) have exploded in recent years. Your teams must master more and more topics. AI is not here to replace your technical teams, but to serve as their support point to bear this growing burden. If you scale back now, know that your competitors will maintain their teams and use AI to move twice as fast and better. Don't give them the opportunity to crush you.
5. Strategy before compliance
Finally, do not see this article as an immediate "To-Do List." That would be entrepreneurial suicide for a startup that is just starting out. The secret is to align your technical maturity with your business target. Focus your efforts on your Product Market Fit with clients within your reach, collect your first revenues, and use this traction to finance, brick by brick, your technical upgrade.
Compliance is not an end in itself; it is a growth lever that must be activated at the right time.
Good fishing! 🎣

Let's talk about your project
Do you want to know more or discuss your project?
Contact us via our contact form.
We will be happy to discuss your goals with you and offer tailored solutions.